Overview
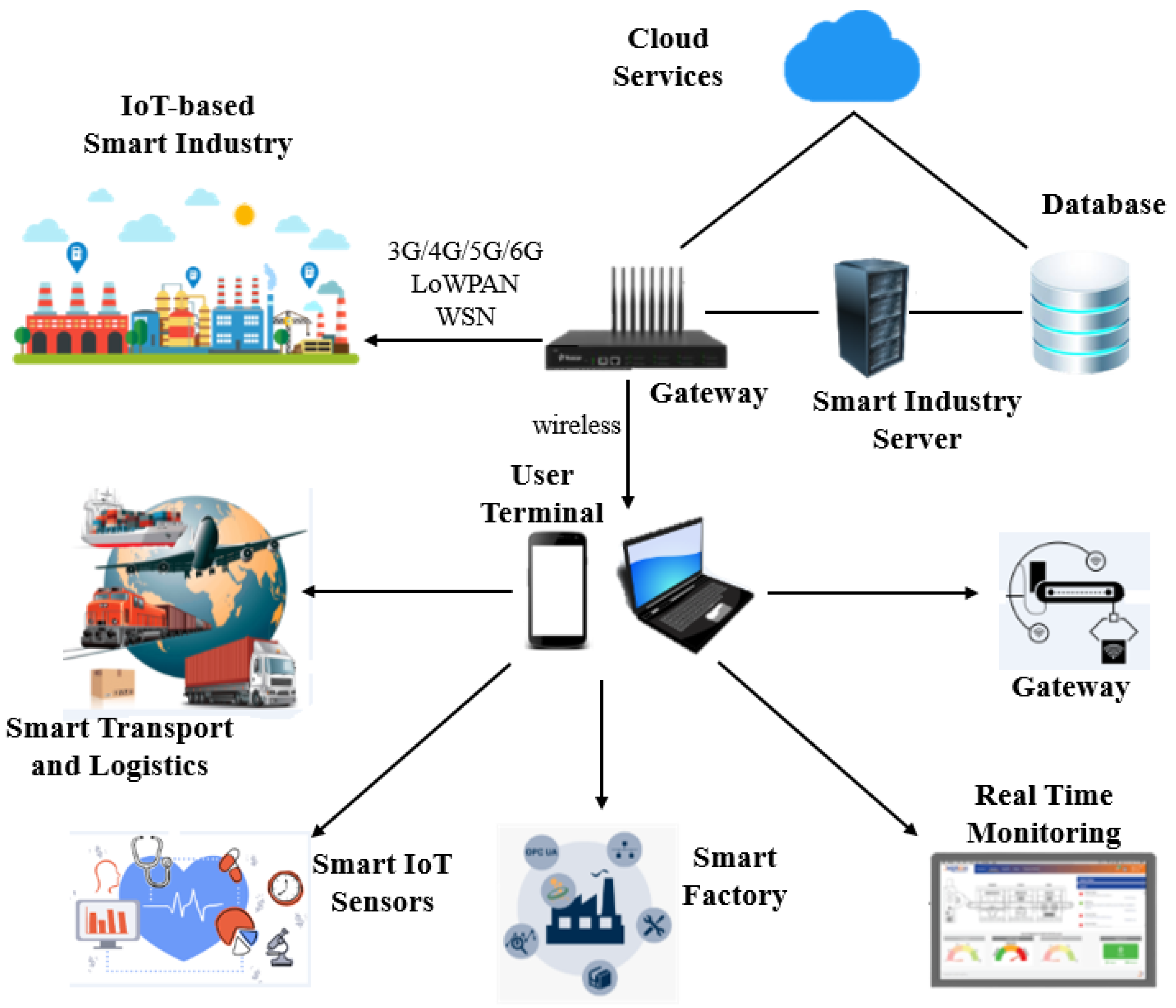
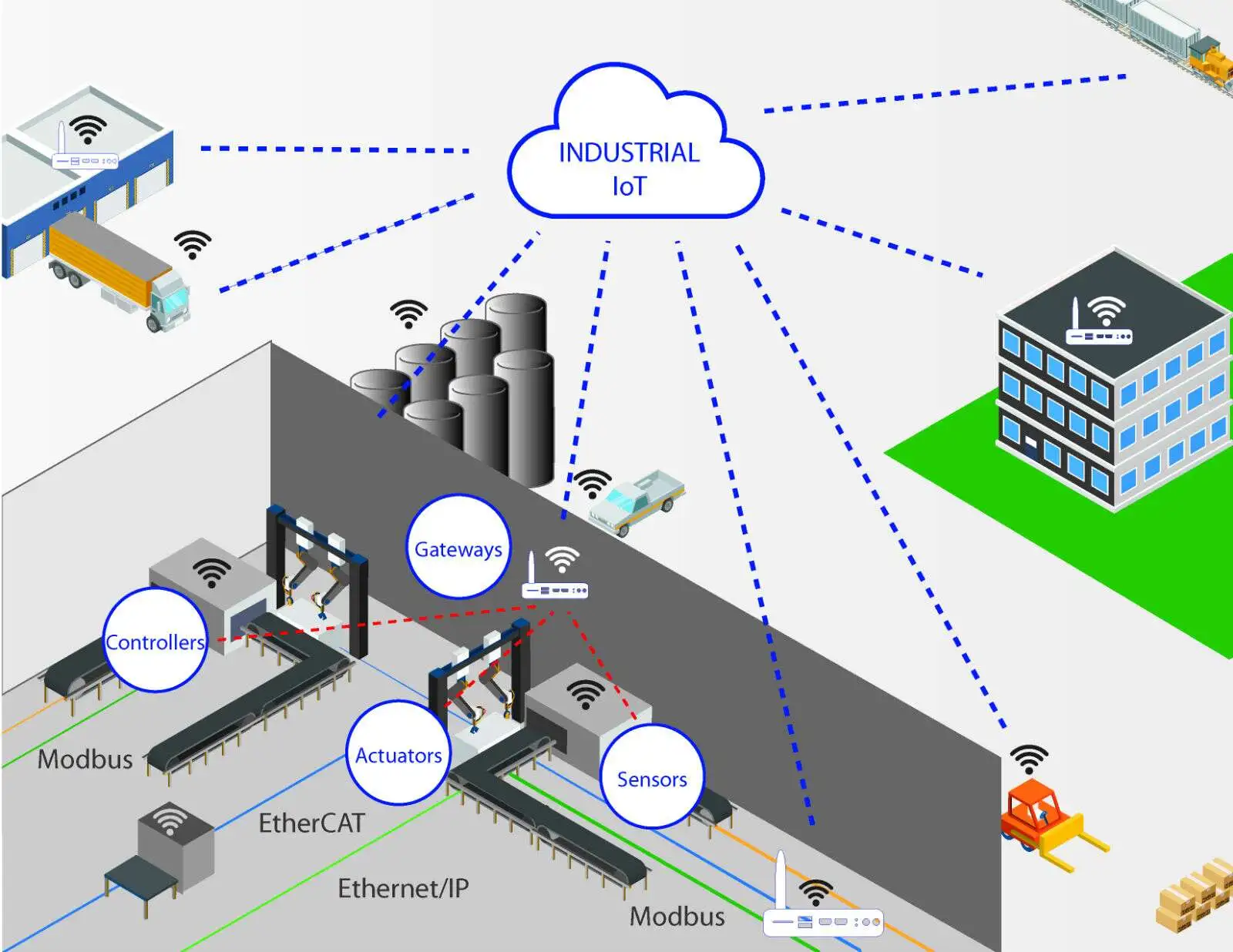
IoT technologies bring significant benefits to manufacturing, transportation, oil & gas, healthcare, agriculture, energy, and utilities. These sectors feature complex infrastructures that aggregate large numbers of connected devices, sensors, smart meters, industrial robots, and communication and data-transfer software. Because IoT systems hold substantial sensitive information, they are frequent targets for attackers.
For organizations deploying IoT, compromise of a single small device can jeopardize all connected devices and systems across an organization and potentially impact partners and suppliers. As industrial IoT (IIoT) scales rapidly, protecting these edge devices is a major industry challenge.
IoT Security Risks and Their Impact
IIoT is expanding quickly; estimates foresee billions of factory-connected devices by 2030. As infrastructure is digitized, cybercriminals target these smart devices with attacks aimed at various components of the IoT ecosystem, including communication networks, operating systems, application software, and the connected endpoints themselves.
Vulnerabilities in IIoT environments create opportunities for attackers to exfiltrate confidential information or cause loss of sensitive data, such as manufacturing blueprints or critical business information. Unauthorized access to a manufacturing network can allow adversaries to alter device configurations, producing potentially irreversible consequences for product quality and operations.
Typical IIoT security issues include unauthorized access via open ports, buffer overflows, denial-of-service (DoS) and distributed DoS (DDoS) attacks. Insecure network interfaces, unencrypted data, and weak authentication are common entry points. Understanding these inherent vulnerabilities is essential for organizations to adopt targeted mitigation strategies.
Industry awareness of IIoT security is growing. According to Markets and Markets, the global industrial cybersecurity market was about $16.3 billion in 2022 and is expected to grow at a 7.7% compound annual growth rate (CAGR) from 2023 to 2028, reaching $24.4 billion by 2028. Current IIoT deployments face five major security risks:
- Data siphoning: Attackers can intercept data in transit at endpoints. When transmitted data is highly sensitive, interception can cause severe damage. Sectors such as healthcare, safety systems, and aerospace are particularly vulnerable. Mitigation includes policies enforcing appropriate encryption for all data in transit and at rest.
- Device hijacking: When sensors or endpoints are hijacked, attackers can exfiltrate data or take control of manufacturing processes, undermining quality control. Preventive measures include regular firmware and hardware updates, and deployment of hardware-based VPN or secure tunneling solutions that integrate more safely with legacy systems.
- Distributed denial-of-service (DDoS) attacks: Endpoint devices can be flooded with network traffic and become unable to perform normal workloads. For example, insecurely connected industrial thermostats can be used in coordinated DDoS attacks that lead to system outages. Network-level defenses such as properly configured firewalls and traffic filtering can mitigate this risk.
- Device spoofing attacks: If an attacker impersonates a trusted device in communications between centralized networks and IIoT endpoints, false commands or data injections can occur. Hardware-based security solutions for device authentication and identity management help defend against this threat.
- Physical device theft: Numerous physical endpoints exist in IIoT deployments; if they are stolen, stored keys or sensitive data on the device can be exposed. Reducing stored sensitive data on endpoints, or using cloud-based key management and storage, lowers the risks associated with device theft.
Commonly vulnerable elements in IIoT infrastructure include monitoring and data-acquisition devices, programmable logic controllers (PLCs), distributed control systems (DCS), and human-machine interface (HMI) networks and mobile interfaces. Among security measures, encryption is often underestimated; weak encryption and authentication frequently lead to data breaches.
Hardware-Based IIoT Security Strategy
Edge computing enables IIoT scale by handling local data processing and analysis, often using machine learning algorithms to enable timely decision-making. Edge devices therefore require strong computing capability and must protect highly sensitive data, which calls for integrated protection techniques that guarantee system security.
Hardware-based security approaches are generally more robust than software-only methods. Edge devices often have sufficient processing power and memory to run advanced security functions. Depending on the application, devices may use microcontrollers (MCUs) for low-power operation or microprocessors (MPUs) for higher compute requirements, and many modern devices combine both.
Security features can be provided at silicon and firmware levels. Embedded security elements or secure modules integrate roots of trust into devices, establishing a chain of trust from silicon to cloud. Hardware-based security enables trusted boot, execution of secure applications and operating systems, secure lifecycle management, and secure connectivity to cloud services and back-end infrastructure.
On the edge, hardware security functions are typically integrated into MCUs and MPUs as security IP blocks. These blocks can provide programmable root-of-trust cores, physically unclonable functions (PUF), random number generators (RNG), unique IDs, SSL/TLS support, and cryptographic engines.
Hardware Solutions for IIoT Security
ChipDNA is a patented PUF technology from Analog Devices (ADI) that resists invasive physical attacks. It leverages random variations in semiconductor device characteristics that occur during chip manufacturing to generate unique, repeatable outputs across temperature and voltage conditions.
In a PUF-based ChipDNA security verifier, each key is represented by a precise analog characteristic of the IC, making it resistant to invasive attack tools and reverse engineering. Each IC has a unique key generated by ChipDNA, which is repeatable under normal operating conditions and provides strong protection against invasive and reverse-engineering attacks.
Earlier products such as the MAX32520 MCU used ChipDNA output as key material to encrypt device-stored data and could optionally use that key as an ECDSA private key for signing operations. In addition to hardware cryptography, the MAX32520 series included a FIPS/NIST-compliant true random number generator, environmental and tamper-detection circuits to support system-level security. That product line is being phased out and replaced with newer devices.
The next-generation MAX32630 family uses an Arm Cortex-M4 core with FPU, designed for low power and efficient signal processing. Secure variants MAX32631 and MAX32632 include a Trust Protection Unit (TPU) with cryptographic accelerators, including a modular arithmetic accelerator (MAA) for fast ECDSA, a true random number generator (TRNG), and a hardware AES engine. The MAX32632 also offers a secure bootloader for additional lifecycle and deployment security.
Encryption is a foundational control for protecting data confidentiality, integrity, and authenticity in the IoT ecosystem. Encryption keys that perform secure boot, authentication, and over-the-air updates must be protected. Chip-level hardware protection of keys is a standard approach to achieving strong security in embedded systems.
As an example from another vendor, the NXP LPC5500 series MCU integrates security modules while maintaining performance. Built on Arm Cortex-M33 technology, LPC5500 improves architecture and integration, reduces power consumption, and offers enhanced security capabilities including SRAM-based PUF roots for trust and configuration, runtime operation of encrypted images from internal flash, and asset protection via Arm TrustZone-M, making it suitable for security-sensitive industrial IoT applications.
Edge devices with secure processor capabilities can meet diverse security requirements across industrial, automotive, consumer, and smart-home use cases. Regulatory and standards pressures are increasing, driving demand for secure device manufacturing and lifecycle management. The focus is not only on secure device operation but also on delivering trusted compute to protect sensitive edge data.
Market analysis from Straits Research indicates a confident outlook for IIoT security, estimating a 29.8% CAGR from 2023 to 2031 and projecting a global IIoT security market size of approximately $122.3 billion by 2031.
While hardware measures are emphasized here, practical IIoT security programs typically combine hardware, software, network, and cloud controls. However, embedding hardware-based security modules in devices is often essential to establish a trusted IoT ecosystem. As secure processor technology matures and cost and complexity decline, hardware security will be more widely integrated across applications and support further innovation.
 ALLPCB
ALLPCB