Overview
The IoT has opened new areas in the digital domain by integrating the physical and digital worlds through a growing number of smart devices. However, as networks expand from smart homes to industrial equipment, a pressing issue remains: security.
As more devices are added to this complex network, security vulnerabilities become increasingly apparent. Edge computing provides a practical response by localizing processing and reducing the inherent risks associated with transmitting data across wide networks. By shortening transmission distances, it reduces opportunities for interception and unauthorized access.
This article examines how edge computing strengthens IoT devices against security vulnerabilities, outlines edge security mechanisms, and summarizes relevant technologies, industry best practices, and real-world applications.
Understanding IoT Device Vulnerabilities
Although IoT devices are useful, they present multiple exploitable points. Common attack surfaces include:
- Network attack surface: The entire path from device nodes to servers can be vulnerable. Each network point should be treated as a potential weakness.
- Software attack surface: Code running on devices and servers may contain vulnerabilities that can be exploited to cause breaches.
- Physical attack surface: Devices are subject to physical attacks, such as debug probing or invasive hardware tactics. If not properly shielded, attackers can gain full access to a device.
Because attackers can choose multiple entry points, a comprehensive, multilayered security approach is essential for any IoT deployment. Device complexity and the lack of widely adopted standards make this difficult to achieve.
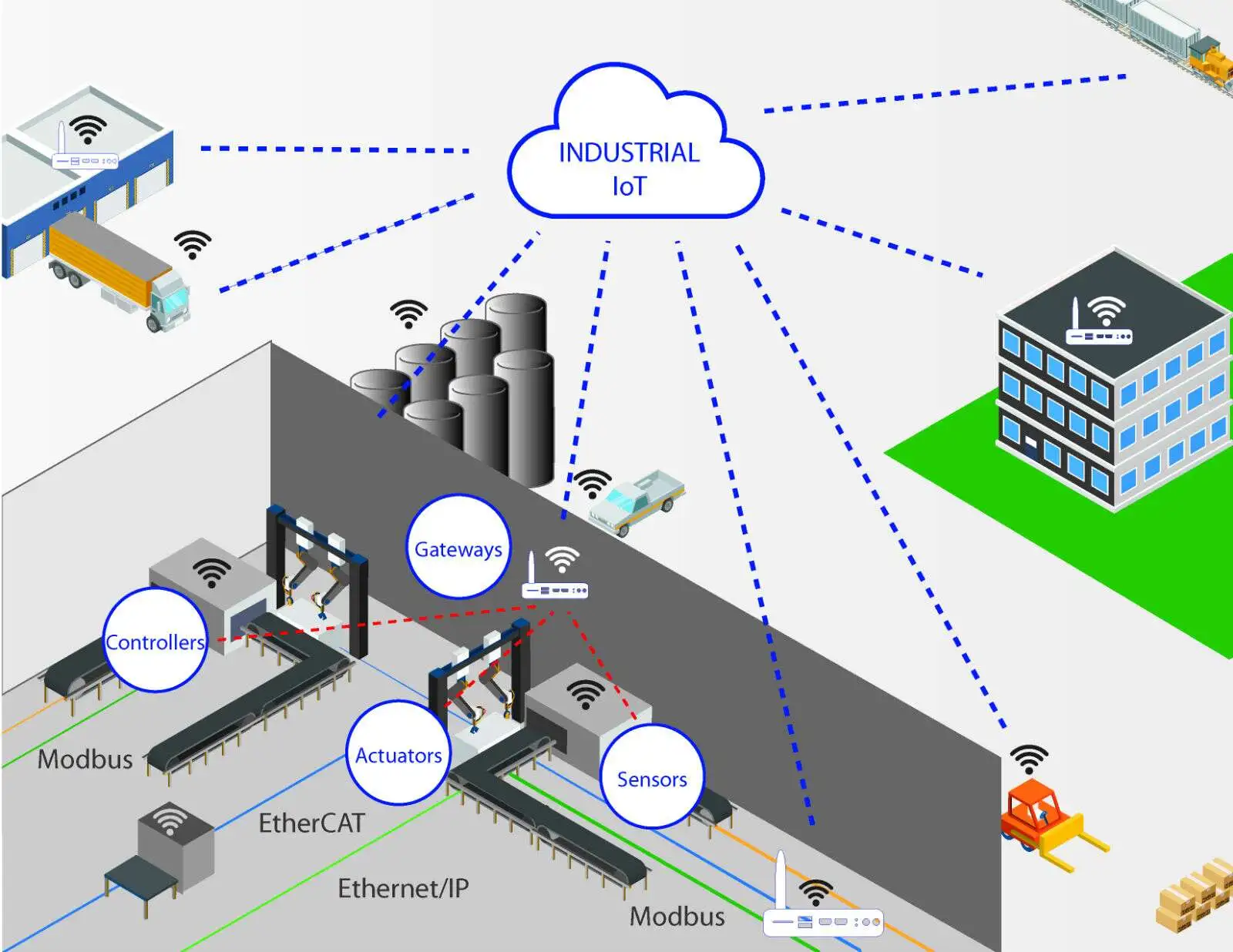
Diversity and Complexity of IoT Devices
IoT devices vary widely, from sensors in wearable fitness bands to factory controllers and vehicles. This diversity is evident across hardware, operating systems, software types, assurance levels, and security protocols.
Security measures differ depending on device function and the potential impact of a breach. Simple devices like smart bulbs may require minimal security, while other devices need stronger features such as link encryption, secure data storage, and hardware roots of trust.
Local Processing for Embedded IoT Devices
Integrating edge computing into IoT architectures is a strategic response to data security requirements. Unlike traditional cloud-based systems where data must travel long distances to centralized data centers, edge computing enables embedded IoT devices to perform processing at the source. This reduces latency and creates reinforced barriers against potential security threats.
Local Processing Capabilities
In an edge environment, data processing occurs closer to where information is generated. This allows real-time analysis and decision-making, improving responsiveness and efficiency for embedded IoT devices.
For example, in a manufacturing environment, IoT sensors on machines can process data locally instead of sending it to a central server. That provides immediate, actionable insights and enhances operational efficiency.
Improving Data Security
Local processing keeps data within a controlled, closed environment, reducing the need for wide network transmission and lowering the risk of interception or unauthorized access. This is particularly important in sectors where data integrity and confidentiality are critical, such as healthcare, finance, and defense.
Modern Technologies for Edge Security
The rise of edge computing has driven development of technologies to strengthen edge security.
Encrypting data at the edge ensures sensitive information remains unreadable if intercepted. Modern edge devices often include robust cryptographic tools that can be configured to meet specific industry or application requirements.
Implementing strong authentication protocols ensures only authorized entities can access data, adding another security layer. When delivering or accessing documents internally, using digital signatures based on public-key cryptography helps ensure documents cannot be tampered with by external parties.
Network segmentation can limit the spread of a potential breach by isolating different parts of the network. Segmentation enables better control and auditing of data movement within a network and supports proactive threat mitigation.
Regular security audits and timely software updates help ensure edge devices operate with current and secure configurations, which is essential for keeping pace with evolving threats.
Industry Best Practices
Adhering to best practices is essential to maintain a robust edge security framework. Common strategies include:
- Multi-factor authentication: MFA increases security by requiring multiple forms of verification before granting access, reducing the risk of unauthorized entry even if passwords are compromised.
- Use of AI and machine learning: AI and ML algorithms enable continuous monitoring and anomaly detection. These techniques can identify unusual patterns and activities faster than manual methods and trigger automated response mechanisms.
Practical Applications
Edge security has practical deployments across multiple sectors. One observable benefit is a reduced risk of breaches for non-technical IoT device users.
Smart cities: Edge computing provides localized data processing in smart city systems, reducing the need to send large volumes of data to central servers. This improves efficiency while maintaining data security for applications such as traffic management and emergency response.
Healthcare: Patient data confidentiality and integrity are critical. Edge computing allows medical devices to process data locally, ensuring sensitive information is handled securely and in real time, which supports patient care.
Manufacturing: Manufacturers use edge computing to process large volumes of machine-generated data locally. Local processing reduces the risk of industrial espionage and helps protect proprietary information.
Protecting Data Integrity in an Increasingly Connected World
In a world that increasingly depends on fast connectivity and instant data processing, edge computing has become a critical component rather than a mere trend.
By implementing localized processing in embedded devices that support IoT, edge computing provides practical solutions to ongoing data security challenges. Its applications span smart cities, healthcare, and manufacturing, demonstrating its practical value and role in preserving data integrity.
Adopting modern edge technologies, committing to industry best practices, and deploying real-world implementations can help organizations improve how they manage and protect sensitive data generated by IoT devices.
 ALLPCB
ALLPCB