Summary
This article analyzes the main security risks faced by mobile devices and mobile communications in the 5G environment, and reviews the current status and limitations of mainstream device security technologies such as system isolation and virtual private networks. It proposes an integrated terminal security solution to meet high-security requirements for mobile communications and mobile office use, consisting of hardware-based system isolation, a guard-style intranet VPN access mechanism, and an inter-system secure communication scheme. The solution addresses hardware, operating system, application, data, and network communication security.
Introduction
With the proliferation of 5G device types and application scenarios, mobile devices have evolved from communication-centric terminals for calls and messages into smart devices used across daily life and professional domains. Device architectures have also changed significantly: SoCs have become more integrated with richer functional modules, and operating systems have become more feature-rich to support increasingly complex applications and services. Organizations are leveraging mobile connectivity for its mobility, convenience, and flexibility by connecting mobile devices to corporate internal networks, using them to handle work and production tasks, and storing corporate data on those devices.
5G mobile devices present information security risks. Balancing the convenience of mobile connectivity with the need to protect communications, data, personal privacy, corporate intellectual property, and national information is a key challenge in mobile information security. This motivates research into mobile device security technologies. This article examines the security risks facing 5G mobile devices and mainstream terminal security approaches, and proposes a dual-hardware, dual-system guard-style isolation and internal network access architecture to support protection of personal privacy, business secrets, and national cryptographic assets.
Security Risk Analysis
When staff use mobile devices to access corporate intranets and store intranet data locally, lack of effective protection for communication channels and local storage exposes intranet data to the internet and creates significant information security risks. Therefore, mobile devices, corporate intranets, and the communication between them all require security protections. Main security issues encountered during device-to-intranet communication include:
- Authentication risks. Passwords, verification codes, or biometric methods can be cracked or spoofed. If a device is impersonated when accessing the intranet, data leakage can occur.
- Data storage risks. Mobile devices often lack fine-grained control over stored data. Data is frequently saved in plaintext without confidentiality or integrity protections and can be modified or stolen by malware. Physical loss of a device also increases data exposure risk.
- Communication risks. Mobile communication includes wireless data, voice, and messaging, as well as short-range interfaces such as Bluetooth, infrared, and NFC. Uncontrolled network and device factors make user traffic susceptible to interception and tampering.
- Device hardware and software risks. Mobile devices use platforms such as iOS, Android, and Arm-based hardware. Reported vulnerabilities and potential backdoors in these platforms represent substantial security concerns.
Overview of Security Technologies
Mainstream terminal security approaches fall into two categories. One is terminal virtualization and system isolation, where a single piece of device hardware runs multiple isolated operating environments so that different systems and their data are isolated. The other is virtual private network (VPN) technology, such as VPDN and VPN, which protect device access to corporate intranets and secure network transport.
2.1 Terminal System Isolation
Most current mobile devices support a single operating system with application sandboxing to separate apps. For example, Android extends the Linux kernel security model with user and permission mechanisms and assigns each app a unique Linux user ID (UID) so apps run in separate processes.
With virtualization and improved device capabilities, running multiple isolated environments using virtual machines (VMs) on a single device has become feasible. VMs create isolated, controlled runtime environments so that applications are not affected by external risks. Access between VMs must occur via defined inter-system interfaces, which simplifies monitoring. Virtualization platforms can use agents to monitor VMs, perform malware scanning, and prevent VMs from escaping to access hypervisor or platform resources.
A dual-system terminal runs two mutually isolated operating systems on one mobile device to support both work and personal use. One system is a secure work system; the other is a personal system. Each has separate runtime environments, file systems, and storage to isolate applications and data. The secure system can restrict hardware features at the driver level (for example disabling microphone, camera, or Bluetooth for the work environment). The device manages switching policies and applies independent security controls to each system to reduce information security risk.
Virtual Private Network Technology
After years of development, VPN technology has two mature architectures: IPsec and SSL/TLS. In the TCP/IP stack, IPsec operates at the network layer and secures IP packets to form a protected virtual transport channel, providing packet confidentiality and integrity via cryptographic algorithms. SSL and its successor TLS operate between the transport and application layers and provide transport security and data integrity for network communications.
VPNs enable secure device access to enterprise intranets and protect network transport. The enterprise authenticates device identity by methods such as MAC address, IP address, username/password, biometrics, PKI certificates, or USB keys, or combinations thereof. Only after successful authentication can the device initiate VPN communication. During VPN sessions, IPsec or SSL/TLS provide:
- Data confidentiality. The sender encrypts data with cryptographic algorithms so that only authorized recipients can decrypt plaintext. Stolen ciphertext cannot be decrypted without keys.
- Data integrity. The sender computes message digests and signatures and sends them with the data. The receiver verifies signatures to confirm data origin and that data has not been altered.
- Replay protection. The receiver can detect outdated or previously received packets.
2.3 Existing Problems
Both system isolation and VPN technologies are constrained by the device hardware architecture. Security mechanisms and policies are typically implemented by the CPU and enforced by the operating system. If the CPU or operating system contains vulnerabilities or backdoors, these security controls can be bypassed and rendered ineffective.
Terminal Security Solution
This section proposes enhancements to 5G mobile terminal security architecture. First, hardware-based system isolation. Integrate two hardware subsystems (including CPU, memory, and storage) into a single mobile device, running the secure system and the personal system on separate hardware to achieve more robust isolation. Second, guard-style intranet VPN access. Insert an encryption coprocessor between the baseband and the secure-system CPU to physically isolate the terminal CPU from the baseband and enforce that communication between CPU and baseband must pass through the security coprocessor, preventing bypass or replacement of the VPN channel. Third, an inter-system secure communication scheme. The secure and personal CPUs communicate via the encryption coprocessor using encrypted protocols for control signals and data exchange.
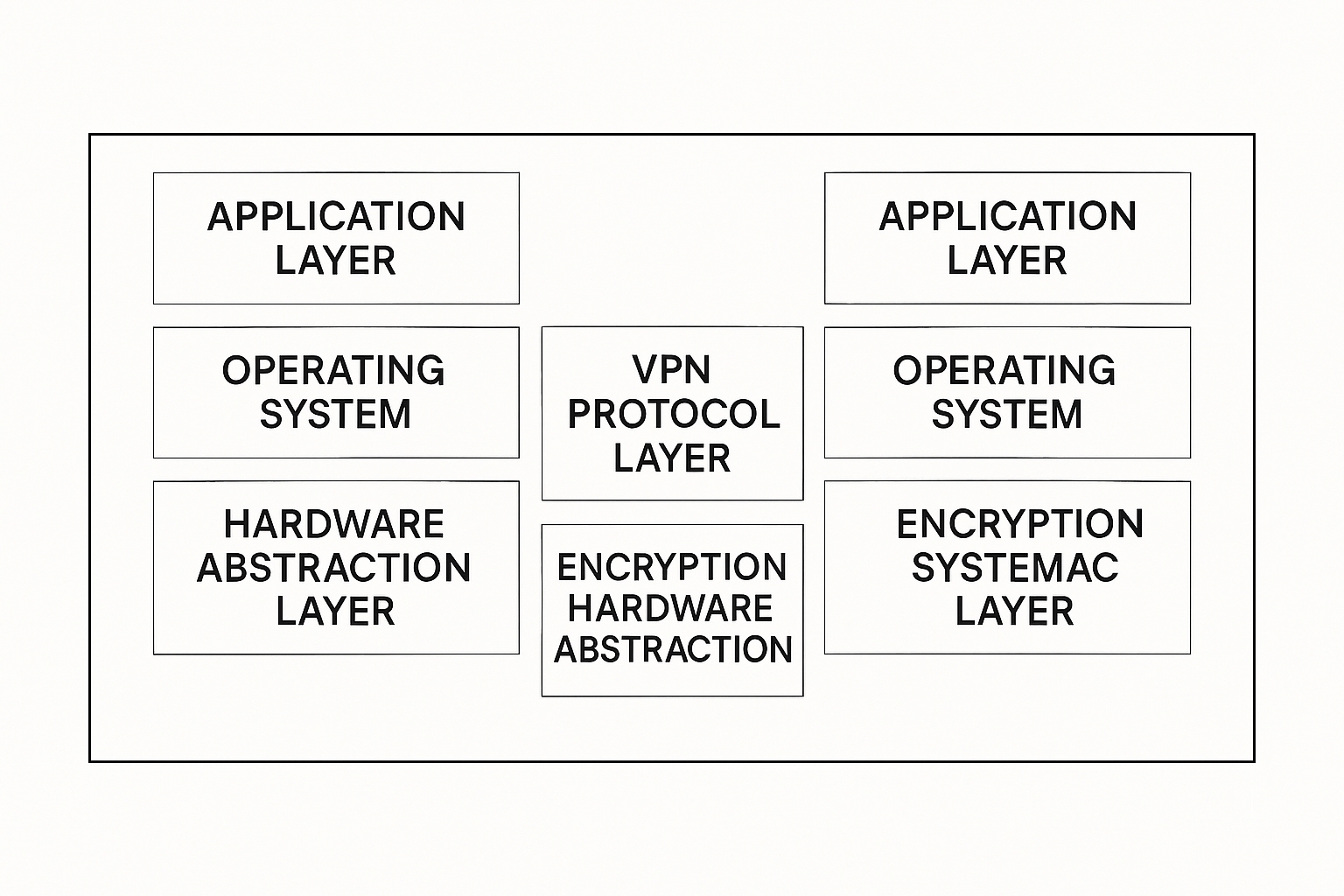
3.1 Hardware-based System Isolation
The secure mobile device integrates two hardware subsystems within one chassis, each with its own CPU, memory, and storage, to run two separate operating systems and associated applications. The hardware can be divided into the secure system, the personal system, a secure communication module (encryption coprocessor), a general communication module (baseband processor and RF module), and system peripherals.
The secure communication module is the security core, connecting the secure system, the personal system, and the general communication module. Its core component is an encryption coprocessor that implements secure data exchange between the secure system and the general communication module, and between the secure system and the personal system, achieving hardware-level isolation between the two systems.
The secure system includes an application processor (CPU), memory, and storage to host enterprise applications, file systems, and data. The secure-system CPU connects directly to the secure coprocessor; all interactions with the general communication module or the personal system must go through the secure communication module. The secure system cannot perform ordinary network communication directly and must establish a guard-style VPN channel through the coprocessor to connect to the corporate intranet. The secure system controls system peripherals directly.
The personal system includes an application processor (CPU), memory, and storage and connects directly to the general communication module. Its basic functionality is comparable to a conventional smartphone. There is no direct physical connection between the personal system and the secure system. Control signals and communication data between them are controlled and mediated by the secure communication module. Secure-system peripherals are not physically accessible to the personal system; when peripheral access is required, it must be authorized and monitored by the secure system.
The general communication module includes the baseband processor and RF module and is functionally similar to that of a conventional smartphone. It transmits communication data that originates either from the personal system or that the secure system forwards via the secure communication module.
System peripherals include power, display, camera, earpiece, microphone, USB, and others, matching common smartphone peripherals. Peripherals are controlled directly by the secure system and can be accessed by the personal system only under controlled conditions.
At the software level, the device separates the secure system, the personal system, and the VPN module. Each system has independent hardware abstraction, operating system, and application layers and runs independently. The VPN module handles secure-system network communications. Placing operating systems on separate hardware yields stronger isolation of runtime environments and storage.
3.2 Guard-style Intranet VPN Access
The secure mobile device supports guard-style secure communication between the device and the corporate intranet, providing controlled access and secure data transmission. While preserving the advantages of mobile connectivity, the device prevents external attacks, unauthorized access, and data leakage. The intranet topology and its position relative to the public internet are shown in the figure below.
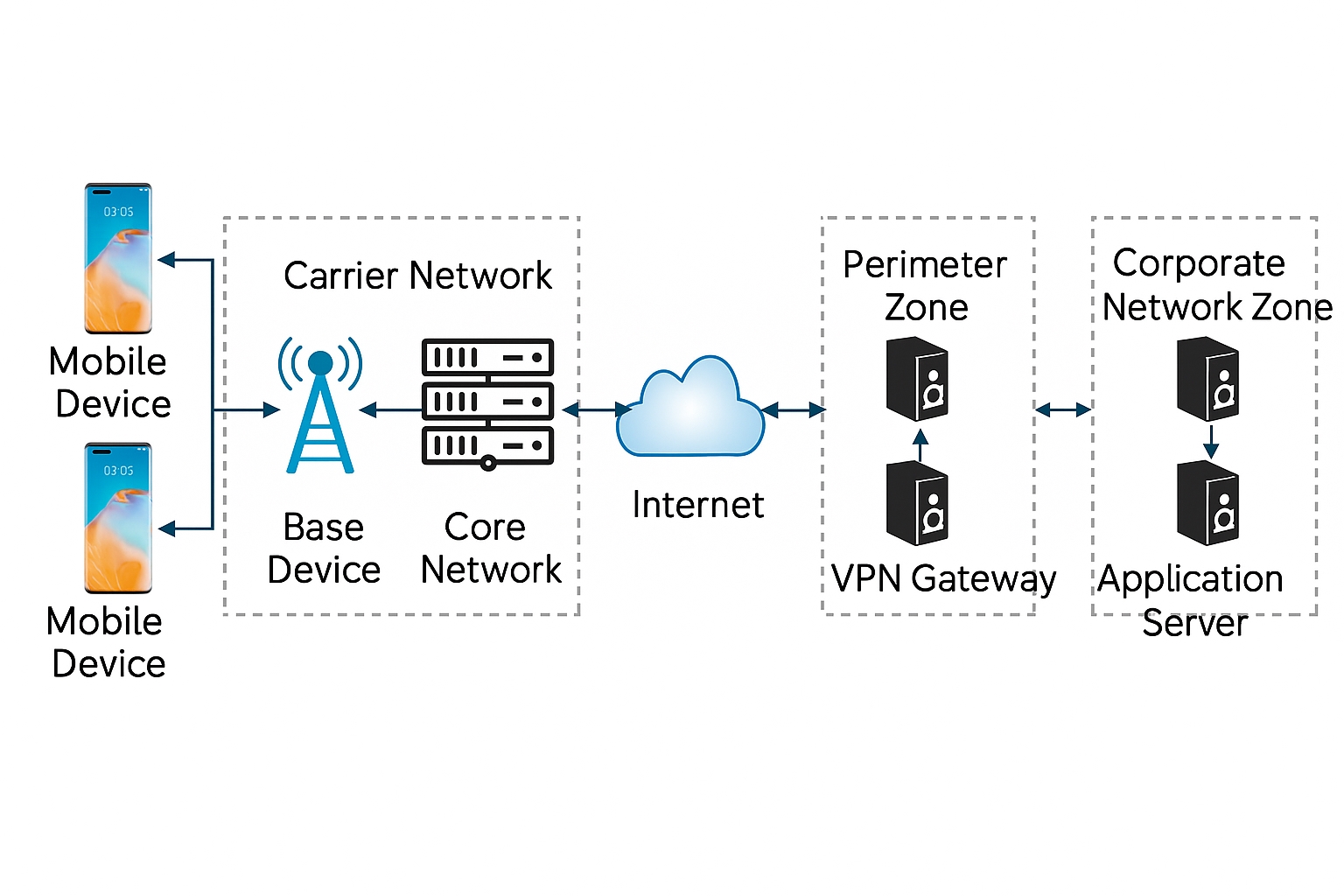
The access zone is the core module for secure intranet access and includes the VPN gateway. The VPN gateway sits between application servers and the internet and acts as the entry point for external users, enforcing user authentication, virtual network tunnel protocols, and cryptographic protections. Secure mobile devices and the VPN gateway exchange intranet data over VPN protocols.
The service zone hosts enterprise business services, primarily application servers, and is functionally similar to standard internet-facing application servers.
The core of the guard-style intranet VPN access is that the communication channel between the device and the intranet VPN gateway cannot be bypassed or maliciously substituted. On the network side, the corporate intranet is physically connected to the intranet access zone (VPN gateway) to ensure physical separation from the internet. Ordinary internet users cannot directly access the intranet. On the device side, the secure system connects to the baseband via the secure communication module (encryption coprocessor). The coprocessor establishes a virtual network channel with the corporate VPN gateway. Virtual network traffic between the secure system and the corporate intranet is carried over the mobile internet, with confidentiality, integrity, and source authenticity preserved for all communications.
3.3 Inter-system Secure Communication Scheme
The secure and personal systems are physically isolated and cannot directly access each other, but limited control commands and certain business data must be exchanged between them. Secure, controlled communication between the two systems is therefore essential.
The encryption coprocessor implements secure inter-system communication, establishing a secure protocol akin to server-to-server communication. Data exchange between systems occurs only when security policies are satisfied, enabling the secure system to authorize peripheral use by the personal system and to send controlled notifications between systems.
Conclusion
This article described the security risks faced by mobile devices in enterprise usage, reviewed common terminal security technologies and their limitations, and proposed a solution that combines virtualization-based system isolation and VPN mechanisms. The proposed measures include hardware-based system isolation, guard-style intranet VPN access, and inter-system secure communication. The article analyzed the hardware and software architecture and functions of the secure mobile device and enterprise intranet. The proposed architecture has been deployed in government communications and office environments with high information security requirements and has contributed to national information security efforts.
 ALLPCB
ALLPCB