Hash functions and SHA
SHA algorithms are widely used in the following applications:
- Git repositories
- TLS certificate signing for web browsing (HTTPS)
- Verifying the integrity of files or disk images
Most hash functions are built on the Merkle-Damgard structure. Here, the input is divided into equal-sized blocks that are processed serially, combining each block with the previously compressed output via a compression function. An initialization vector (IV) seeds the process. By using a compression function, the hash resists collisions. SHA-1 is built on this Merkle-Damgard structure:
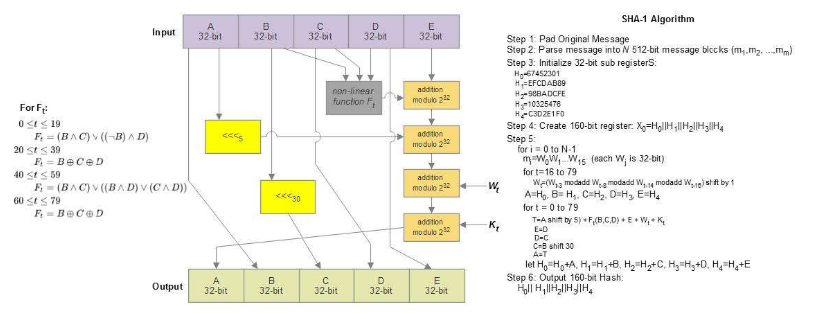
Typically, the SHA algorithm input must be smaller than 2^64 bits. Messages are processed in 512-bit blocks. SHA-1 has been largely superseded by stronger cores such as SHA-256 and SHA-3 after collisions were found. While finding collisions can require around 2^51 to 2^57 operations, renting GPU time for a few thousand dollars can make certain attacks feasible. It is therefore recommended to migrate to stronger SHA variants.
Public key infrastructure
Asymmetric (public-key) cryptography is fundamental to internet commerce and communication. It is commonly used for SSL and TLS connections on the web. Typical uses include public-key encryption, where anyone with the public key can encrypt data that only the private-key holder can decrypt, and digital signatures, where the sender signs data with a private key and any holder of the public key can verify authenticity.
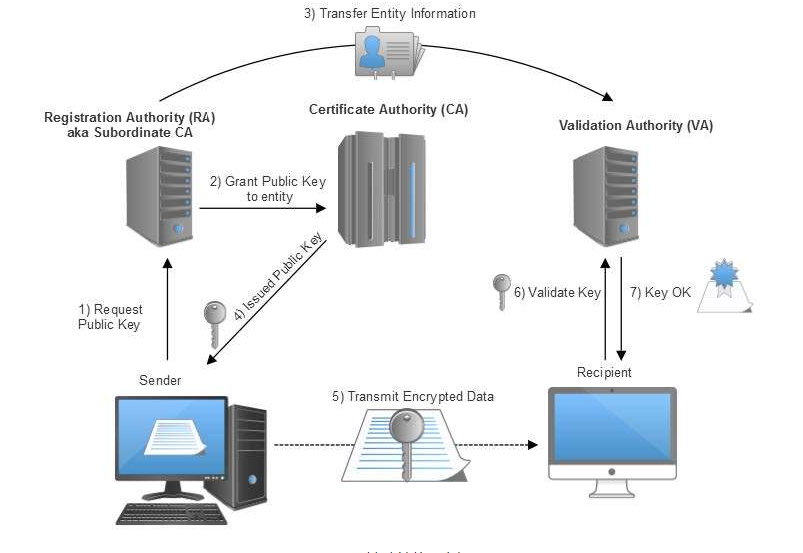
To provide confidence in public keys, a process called public key infrastructure (PKI) is used. A trusted third party known as a certificate authority (CA) manages roles and policies to create and distribute digital certificates. Symantec, Comodo, and GoDaddy are common public issuers of TLS certificates. X.509 is the standard that defines the public-key certificate format and underpins TLS/SSL and HTTPS. X.509 specifies details such as the algorithms in use, expiration dates, and the certificate issuer.
PKI also includes registration authorities (RA) that validate requestors and manage roles and policies, and validation authorities (VA) that communicate revocation lists. The CA issues certificates to senders. When a message is received, the VA can validate the key to ensure it has not been revoked.
Network stack — Transport Layer Security
Transport Layer Security (TLS) appears across many areas, from TLS and DTLS used by MQTT and CoAP to WAN and PAN security. TLS integrates many of the cryptographic protocols and techniques discussed elsewhere. The following briefly describes TLS 1.2 processes.
TLS evolved from SSL, introduced in the 1990s, and was standardized as TLS in 1999. TLS 1.2 is defined in RFC 5246 (2008). TLS 1.2 supports SHA-256 in place of SHA-1 to strengthen hashing security.
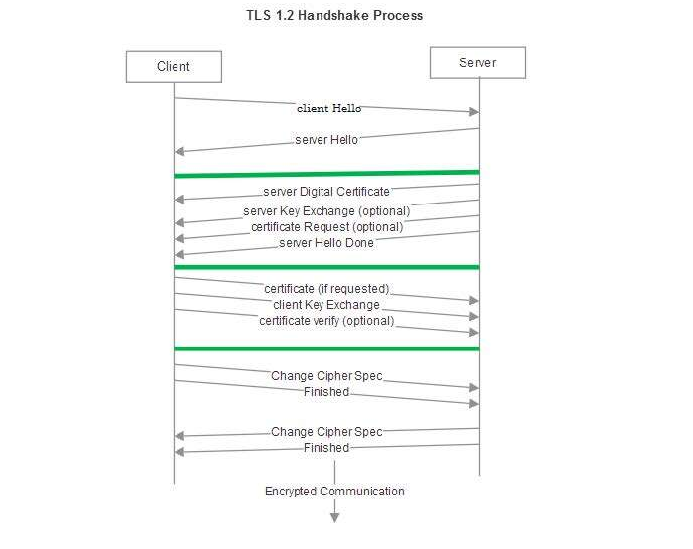
In TLS encryption, the process typically follows these steps:
- The client opens a connection to a TLS-enabled server (HTTPS port 443).
- The client provides a list of supported ciphers.
- The server selects a cipher and hash function and informs the client.
- The server sends a digital certificate to the client, which includes the issuing CA and the server's public key.
- The client verifies the certificate's validity.
- A session key is generated by one of the following methods:
- The client encrypts a random value with the server's public key and sends it to the server. The server and client then use that random value to create a session key for use during the communication.
- A Diffie-Hellman key exchange is used to generate a session key for encryption and decryption. The session key is used until the connection is closed.
- Secure communication begins using the established encrypted channel.
Datagram TLS (DTLS)
Datagram Transport Layer Security (DTLS) is a datagram-based protocol derived from TLS (DTLS 1.2 is based on TLS 1.2). It is designed to provide similar security guarantees for unreliable transport protocols. The CoAP lightweight protocol uses DTLS to ensure secure communication.
 ALLPCB
ALLPCB